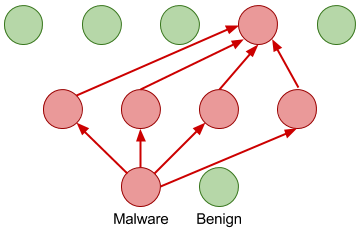
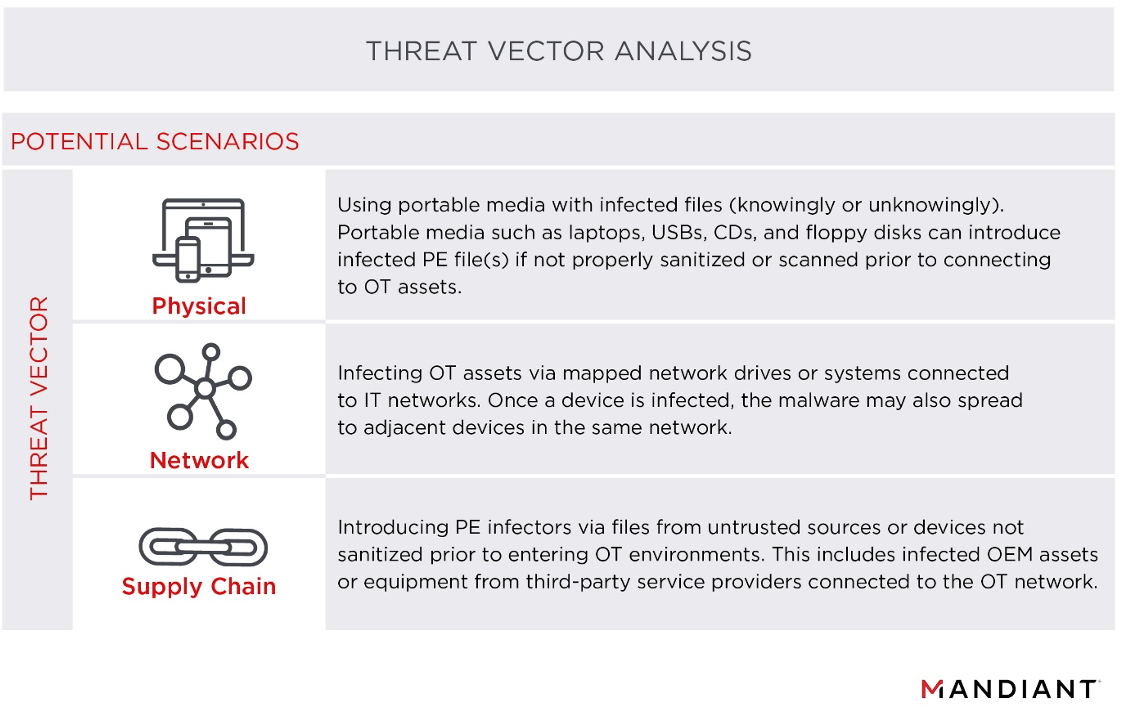
GitHub - ryderling/adversarial-attacks-and-defenses-for-windows-pe-malware-detection: A curated resource list of adversarial attacks and defenses for Windows PE malware detection.
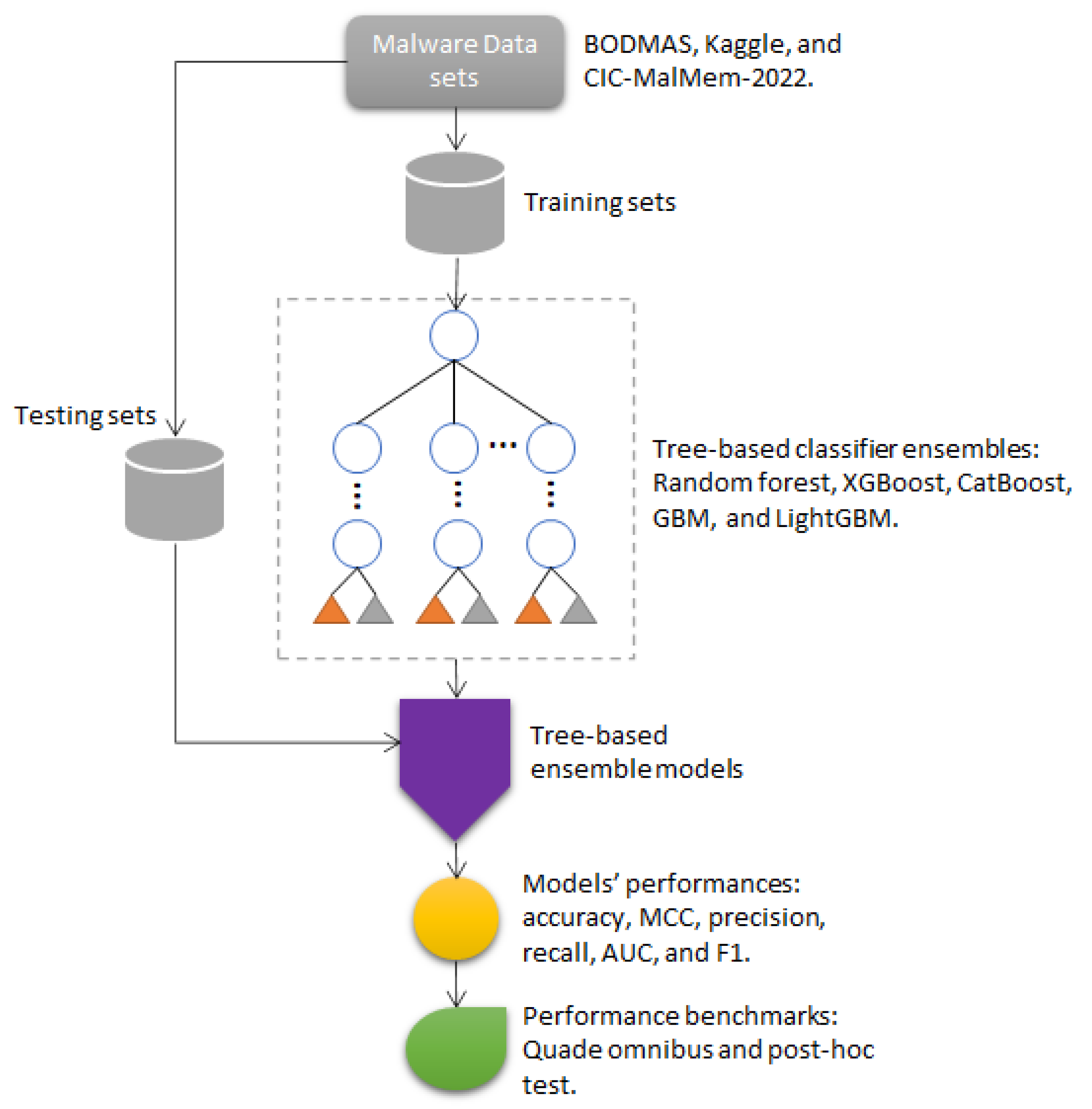
Algorithms | Free Full-Text | Tree-Based Classifier Ensembles for PE Malware Analysis: A Performance Revisit
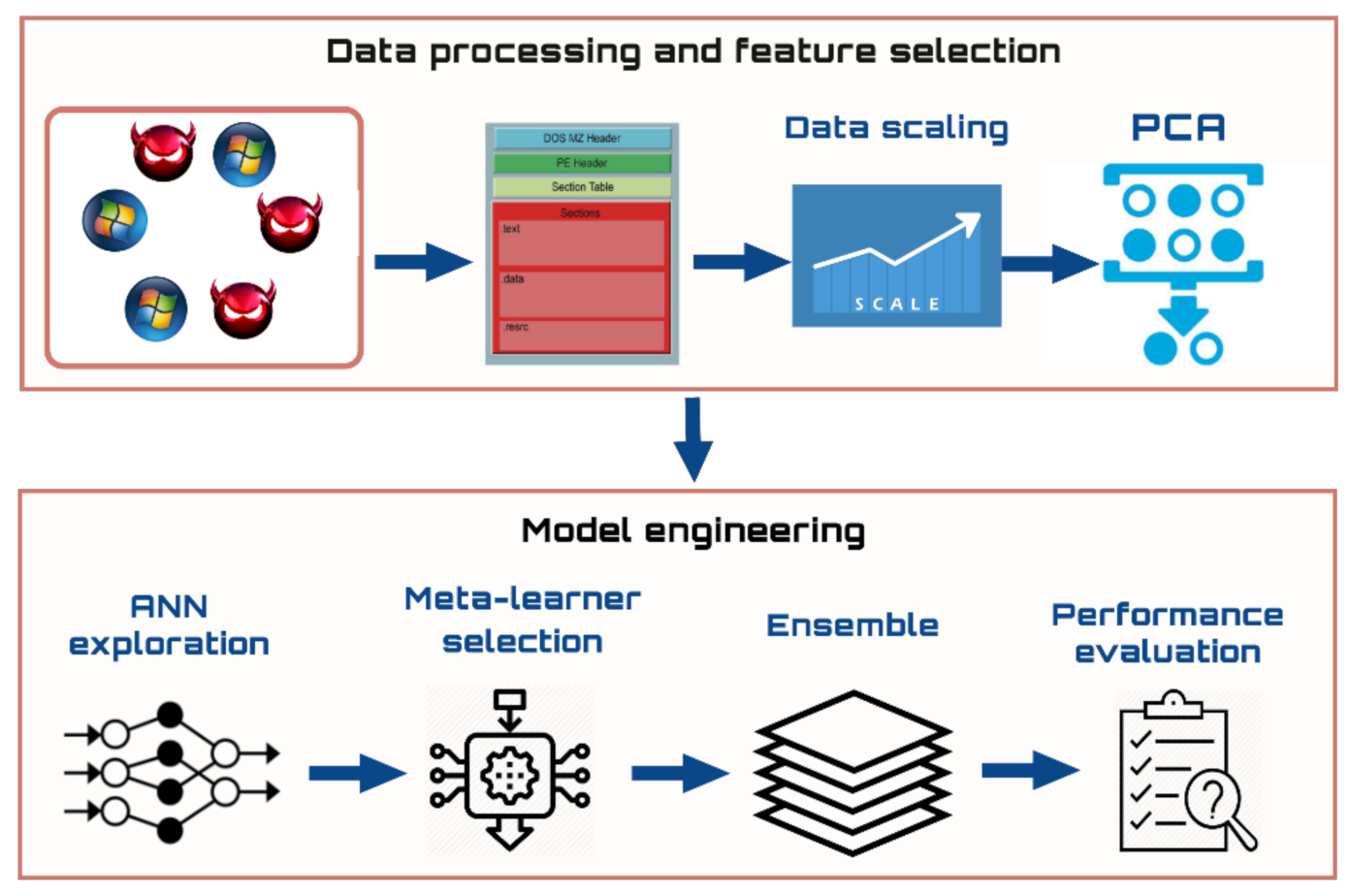
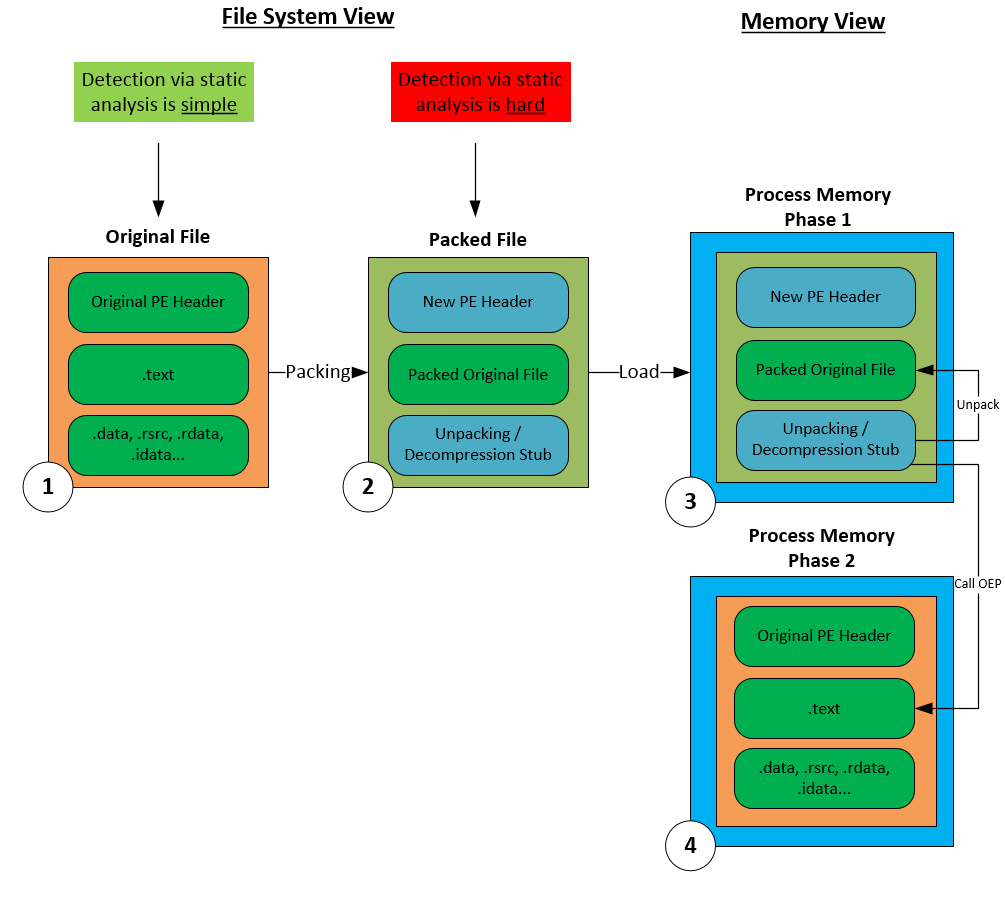



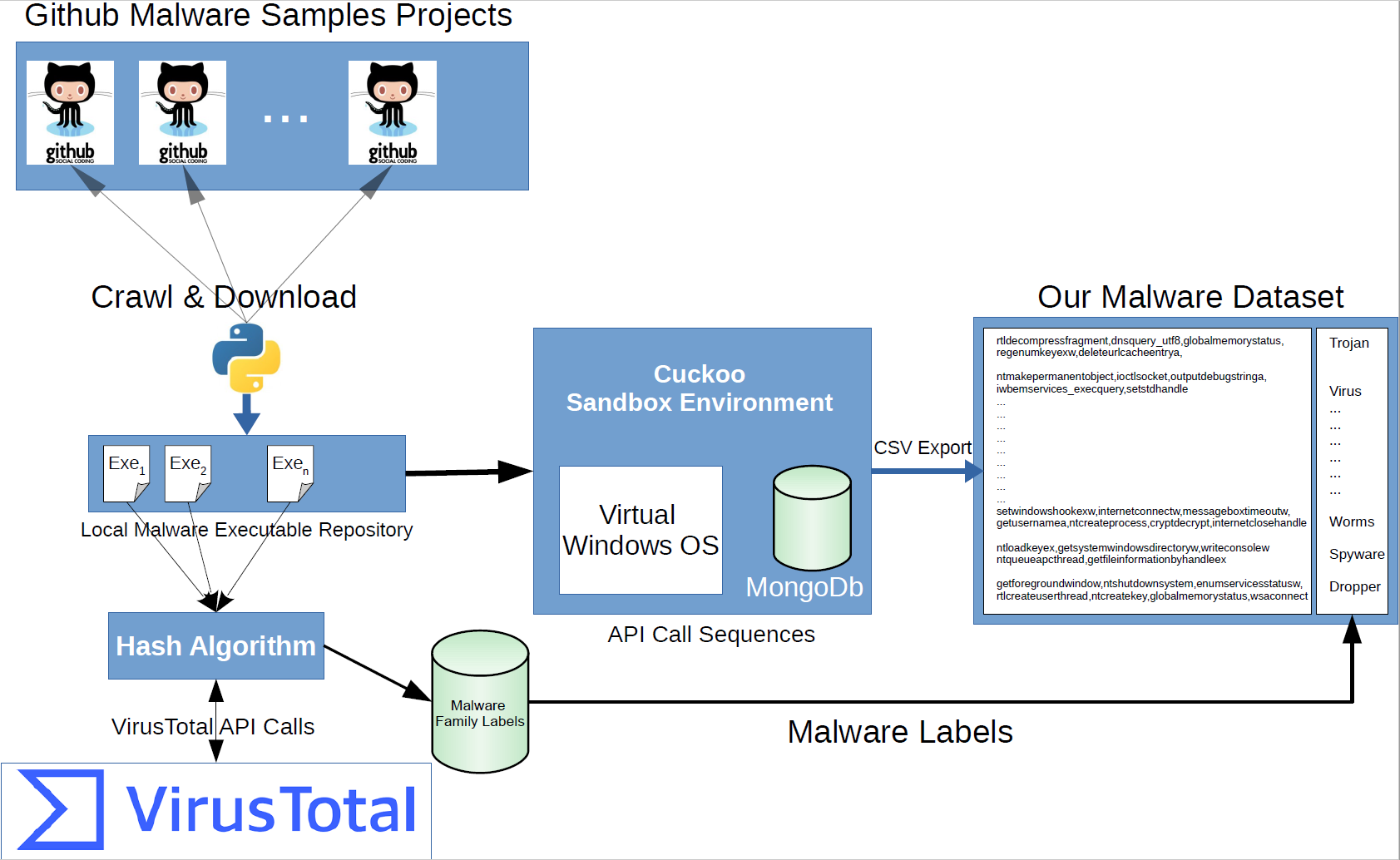



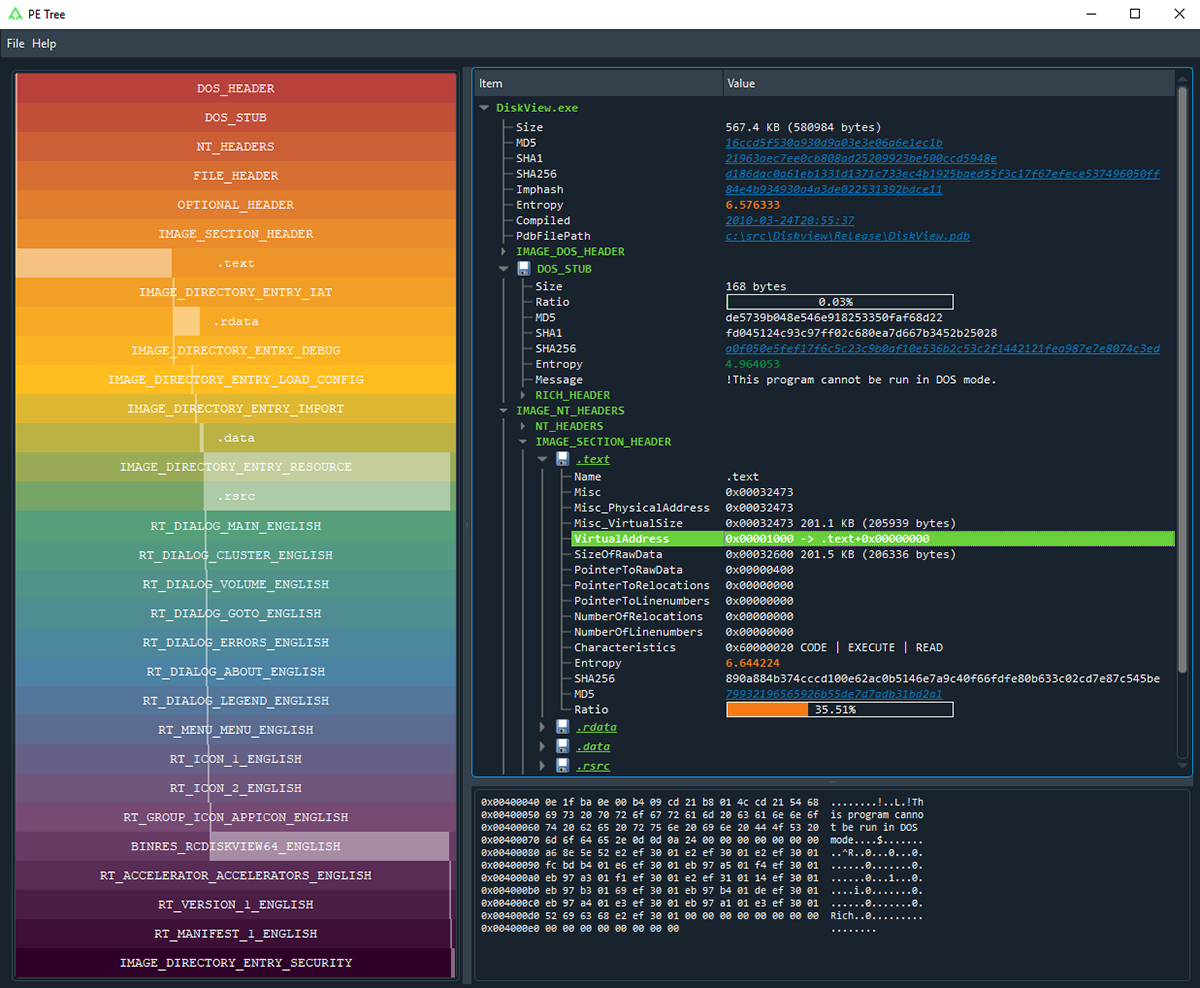


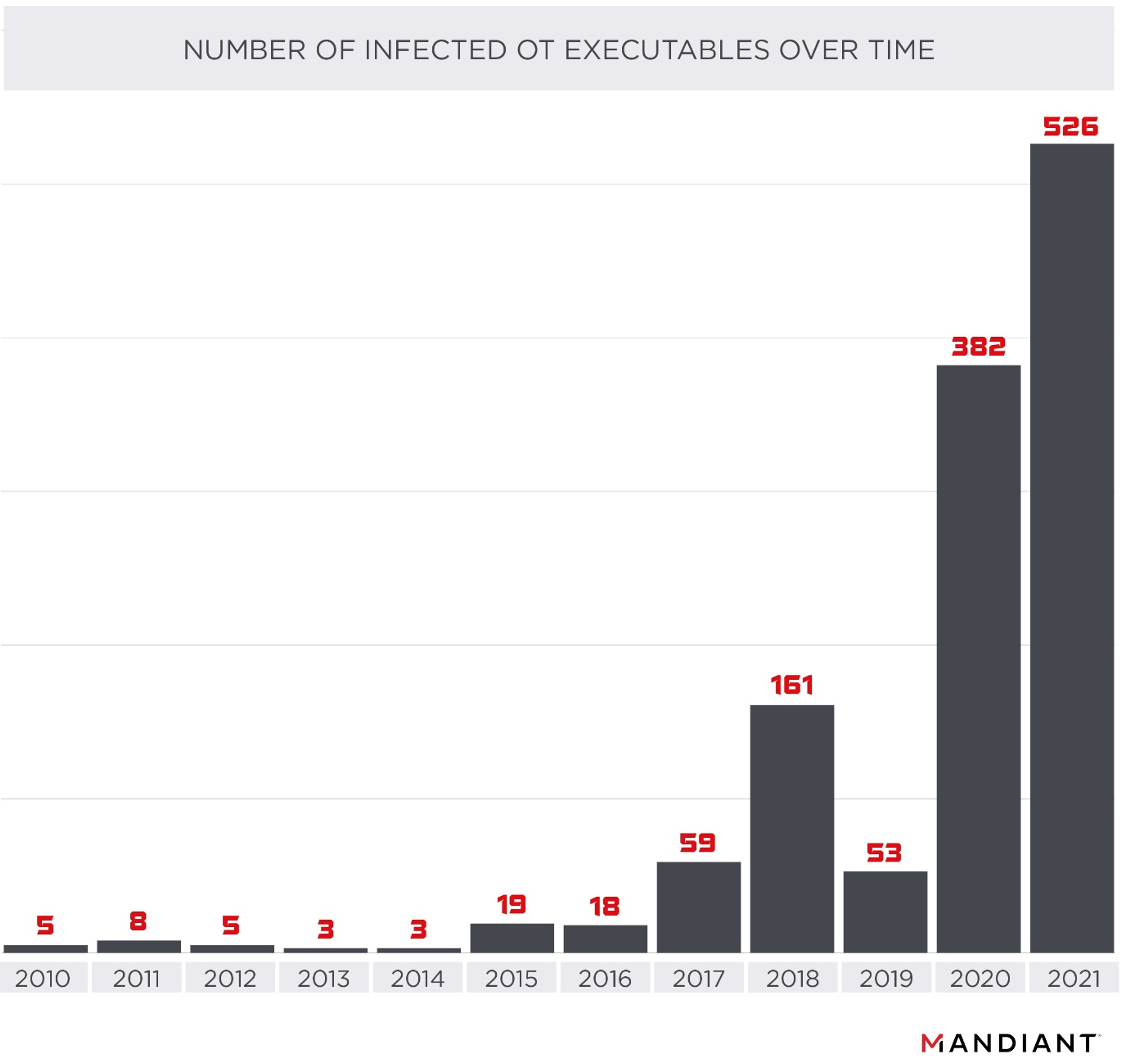

![PDF] Detecting Malware based on Analyzing Abnormal behaviors of PE File | Semantic Scholar PDF] Detecting Malware based on Analyzing Abnormal behaviors of PE File | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e5563cbef39a40fc91a7b4a0510697329132dbe9/2-Figure1-1.png)